These are my notes from VIR307 at TechEd NA 2012, with Bob Combs.
Cloud Demands
- Integration of security and protection
- Ability to add traffic tools
- Unification of management tools
- Blur distinction between physical and virtual networks
My experience: anything manual (setting up VLANs, firewall rules, etc) prevents self-service, and slows down deployment of traditional service. Also adds a great deal of complexity because traditional systems not designed for the scale (networks, rules, tenants) of cloud computing. Anything done in software is automatable and flexible, and could make self-service possible.
The Hyper-V Switch
Replaces the virtual network. Same GUI, does the same basic role (connect virtual network cards to physical networks) … but more:
Remember that the switch port is an attribute of the virtual network card. Therefore your policy moves with your VM.
- PVLAN: Use 2 VLAN addresses to scale out with flatter networks and achieve some level of isolation
- Trunk Mode: The ability to allow multiple VLANs to go to a single VM port.
- Port Mirroring: Forward traffic from one NIC to another. Could be useful for virtual IDS.
- Unified Tracing: Trap packets for analysis.
Interesting note: if you apply a policy on an SR-IOV vNIC then the channel will be rerouted via the virtual switch to apply the policy, thus disabling SR-IOV for that vNIC.
Extensibility
3rd party extensions, not replacements, add extra stuff that MSFT doesn’t do in the switch. The extensions have to be logo tested and certified to make them reliable. The system is “open” to encourage growth in the ecosystem. Already more networking extensions than vSphere has replacements.
Extensions
The extensions are filters – NDIS-based Windows Filtering Platform Providers. Configuration is unique to each instance of an extensible switch on a machine.
3 types of extension:
- Capture: inspect traffic and generate new traffic for report purposes, but cannot modify or drop traffic. Can have multiple capture extensions. They can be ordered/reordered. inMon sFlow Traffic Monitoring is an example for monitoring virtual traffic.
- Filtering: Can inspect (everything that capture can do), drop, modify, and insert packets. 5Nine Virtual Firewall v3.0 is an example.
- Forwarding: Direct traffic, defining destination(s) of each packet. Forwarding extensions can capture and filter traffic. Think of it as all encompassing. What if you wanted the Hyper-V switch to look like another switch? That’s what this type allows. NEC OpenFlow for Hyper-V is an example of this. The Cisco Nexus 1000V is another example.
SCVMM
VMM agent can manage the extensions via extensions to VMM.
PowerShell
VM Based Traffic Tools
- Can run in VM, as a switch extension, or as a host service
- Monitoring Port copies traffic to VM
- Traffic trunked to VM before distributing to other VMs (trunk mode on port)
- Capture extension echo traffic to service
- Extension pipe/tunnel traffic to a destination
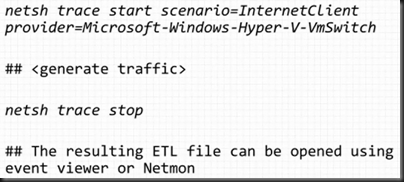
Extensible Switch ETW Tracing Example
Tracing events.
Extensible Switch Unified Tracing Example
Capturing packets.
Summary of Extensible Switch Benefits
There were a bunch of demo videos featuring the partner extensions that I did not take notes on.